Best WordPress brute force plugin (Easy and Best way): WordPress is one of the most commonly used web platforms out there and that in turn makes it an easy target for brute force attack. How to protect your WordPress site from brute force attacks may be on your mind.
A survey shows that 1 out of 4 websites is developed through WordPress. That is like 25% of the entire websites that are available on the internet. But how secure is WordPress? One of the common and notable gripes with WordPress is that it is vulnerable to brute force attacks.
Brute force attack essentially provides the hacker with your login credentials making it very simple for them to gain access and control of your website. How to stop brute force attacks on WordPress websites? Well, that is exactly what we’re going to talk about in this article.
Contents
- What is a WordPress Brute Force Plugin?
- 1- WordPress Firewall Plugin
- 2- Using Strong Username and Password
- 3- Limiting Login Attempts
- 4- Changing the Default Login Page URL
- 5- Two Factor Authentication
- 6- Using the latest version of WordPress
- 7- Password protecting the Directory Panel
- 8- Disabling the Directory Browsing
- 9- Disabling PHP file execution
- 10- Enabling Geoblocking
- 11- Backup Plugin
What is a WordPress Brute Force Plugin?
Simply put, a brute force attack is a trial and error run to get control and access to your website. For this hackers usually resort to specially designed software that sends a large volume of requests to your website. The primary purpose of these requests is to get the access credentials of your website, be it pin, password, or passkey.
Hackers can use this information for varied purposes. It can be to extort you, delete your blog, or use it for other nefarious activities.
Even if the brute force attack fails, the implications for your site can be quite harmful. The overwhelming number of requests will slow down your hosting server and in worst cases, crash it. Higher downtime and low responsiveness will lower your SEO and ultimately divert the traffic away from your site.
In this article, we will review some key steps that you can take to prevent your WordPress site from brute force attacks using various WordPress Brute Force plugins.
1- WordPress Firewall Plugin
As we have already mentioned, one of the biggest issues, even for a failed brute force attack is that it slows down your blog ultimately crashing it or harming the SEO. This happens mainly because of the high number of traffic on your web host.
A firewall plugin will ensure that only legit and real requests get through to your server. A firewall helps to prevent server overload and in turn, saves it from a crash.
You can opt for any of the two available firewall plugins for WordPress.
Application Level Firewall
This is a basic filter tool that filters out the bad requests once they reach your server. This is an efficient WordPress Brute Force Plugin tool but it still runs the risk of overloading your server.
DNS Level Website Firewall
This is the most reliable and widely used firewall plugin out there. DNS-level firewall reroutes the requests through their cloud proxy servers, meaning no requests directly end up in your server. The rerouting helps to identify genuine requests and block off any unprecedented brute force attack.
2- Using Strong Username and Password
This is probably the most common solution to every form of login threat out there – using a strong username and password.
For WordPress, the threat is a bit more substantial as the brute force plugins cannot detect blog content scans from the brute force software. This software is specially designed to look for key phrases within your blog that can be the potential username of your website.
So if you’re thinking you’ll be using your display name as your username, you run a big risk of compromising the security of your blog.
We suggest using a unique username that is not related to your blog nor does it appear anywhere in your blog. This makes it significantly hard for the brute force software to detect your username.
Another common knowledge is to use a strong password. We cannot stress enough how important it is to choose a password that is not just numbers or names. You should follow the guidelines properly to set up a strong password as it can go a long way to safeguard your account.
People often complain that they cannot remember their passwords. We suggest using password managers. There are quite a few paid password managers that can keep your password secured. They will only be one tap away making it easy for you to access them.
3- Limiting Login Attempts
The basic idea behind a brute force attack is simple – trying out combinations over and over again. This solution, however, puts an end to the trial phase in its initial phase. How is it done?
Well, the idea is pretty simple here. To prevent a brute force attack on WordPress, the login attempt is limited to just three. After three login attempts, any new login attempts would require captcha verification which the bots obviously cannot bypass.
This can be easily set up using a brute force plugin. All you have to do is just log in with your credential and set up the plugin. You can also view from which region the bot attacks are happening and this can be used to take more precautionary steps which we will discuss later in the article.
4- Changing the Default Login Page URL
Another key way to deter the incoming brute force attack is by changing the default login page URL. The default login URL as the name suggests is the same for all websites. Needless to say, it makes it very easy for hackers to target multiple pages and that is what they do for maximum infiltration.
The default login page URL can be changed through plugins as well. you can make use of multiple brute force WordPress plugins that are available.
We would suggest you use the WPS Hide Login plugin. All you have to do is login into your website and go to your WordPress dashboard. From there you can go to settings and change the default URL to a custom one.
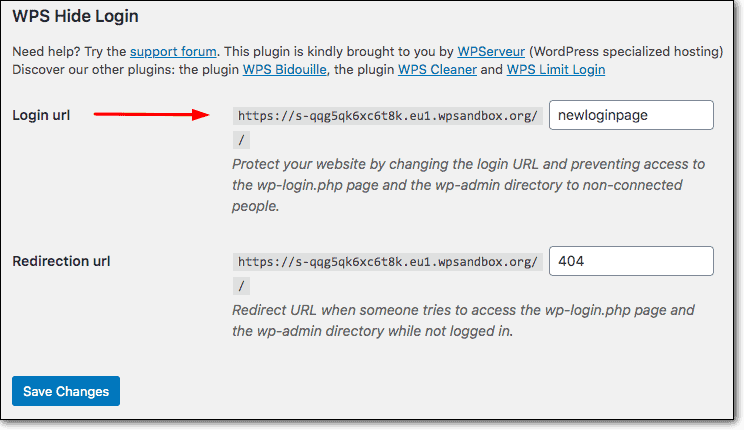
5- Two Factor Authentication
We have all heard of two-factor authentication. This ensures that it’s you who’s trying to access your account in real-time. The two-factor authentication can be enabled for your WordPress site through a WordPress Brute Force Plugin.
With this plugin enabled, you will need to pass an additional step after login into your website. The automated plugin will send a confirmation code to your smartphone that you will need to input to gain access to your website. This ensures that no one other than you can have access to your website.
6- Using the latest version of WordPress
One of the common mistakes of web owners and bloggers is not to use the latest version of WordPress available. This exposes their site to vulnerabilities as it provides the hackers with opportunities to target sites running on an older version of WordPress.
WordPress is an open-source platform that gets security patches and updates regularly. Considering that it would be unwise to not update your platform to the newest stable version.
Security patches are made to cover up loopholes and openings that are a threat to the overall security of the site. So needless to say, it’s very important to have your site updated to the latest version.
7- Password protecting the Directory Panel
Well, it is clear by now that the main aim of a brute force attack is to gain access to the admin area of your website. The admin area is the control panel of the website and all activities get directed from here.
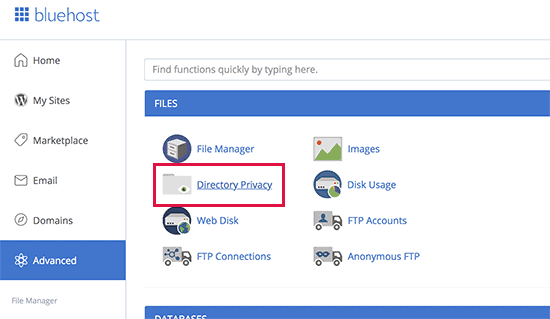
So naturally, you need good protection from the admin panel. However, the plugins that are available only target the primary login to your website.
In addition to the primary login, you can set up an additional login step for the directory panel.
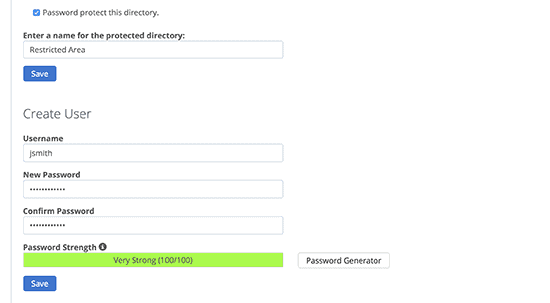
As shown above, you select a directory and choose to password-protect its contents through a separate username and password.
The process is fairly simple, you’ll have to go to the directory Privacy and select wp-admin from there. After selecting wp-admin, the cpanel will ask you whether you’d like to password protect the directory. From there, follow the directions.
8- Disabling the Directory Browsing
Whenever your webserver cannot locate your index files, it showcases an index page. An index page outlines the contents of the directories available within the website.
Needless to say, these directories hold sensitive information regarding your website that can be potentially used during a brute-force attack. As a result, hackers might have uninterrupted access during the brute force attack.
To resolve this issue, you can disable the directory browsing setting. What it does is that it disables the webserver from showing the index page and in turn gives access to the list of files.
To disable directory browsing, you need to open your WordPress dashboard and locate the .htaccess file. After that, you need to include the following line in the file –
Options – Indexes
That’s it. Your directory browsing has been disabled and it is ready to prevent brute force attacks on WordPress
9- Disabling PHP file execution
Almost all of WordPress is written on PHP and hackers target this as a backdoor tool to gain access to your webserver. A PHP script would mean unhindered access to your WordPress site without you knowing through the back door channel.
So how can you stop that? For that, you need to disable the PHP file execution. When you disable PHP file execution, even if the hackers install a script on your WordPress server, they will not be able to run it.
To disable the PHP file execution, you need to write a few lines of codes:
<Files *.php>
deny from all
</Files>
Write it down on a notepad save it as a .htaccess file on your computer and upload it to your server. This will ensure that no PHP scripts can be run on your upload server which is a typical spot for hackers to install their script files.
10- Enabling Geoblocking
Remember we talked about how you can view the region from which the brute force attack is being conducted? Well as it turns out, you can use this knowledge to implement a security measure for your blog.
Hackers indeed exist all around the globe and you cannot exactly pinpoint from where your next attack might happen. But you can work on the knowledge from previous brute force attacks.
Say for example your blog does not target Chinese clients yet you seem to receive an unusually high number of requests from Chinese Ip addresses, you’d be sure to know that your site is under brute force attack.
To combat that, you can use geo-blocking services that would block all the IPs from a specific region making your site safe from attacks for the time being, and stop brute force attacks on WordPress.
11- Backup Plugin
This is probably the last resort in the face of any brute force attack. This is the failsafe option if you fail to prevent a WordPress brute force attack.
As the name suggests, the job of the backup plugin is, well, to backup your files and blogs. WordPress itself offers limited backup options, but that is not reliable and isn’t safe.
However, you can opt to have your backup plugin like UpdraftPlus. Rather than settling for an unreliable backup plan, you can use UpdraftPlus which has its unique backup process which schedules backup at a cloud drive of your choice.
A third-party plugin is not only reliable but also ensures that you can easily access the contents of your blog if it ever falls victim to a brute force attack. Having an up-to-date backup will ensure easy recovery of your website hence reducing the downtime.
See also:
You Do not Have Sufficient Permissions To Access This Page WordPress Error
Final Thoughts
So there you have it, the most comprehensive guide to prevent WordPress brute attacks. WordPress has always fallen victim to brute force attacks, be it startups or well-established blogs. But as we have tried to outline in this blog, it is fairly easy to protect your webserver from such insurrections.
Being a bit careful, and sometimes going the extra distance to secure your web server is all that you need to protect against any unwanted attacks. We hope this guide helps you to see what you’re doing and what you should be doing to secure your website. Happy blogging!





